Changelog
- 2019 Nov 29
- Added "Do you need it?" section and thoughts
- Paginated to 2 Pages
Home(1) is a 2 storey house since before I was born which is around the 1980s, so it is old, tricky and/or impossible to wire the house without breaking anything. As my room is located on the second floor, it is time to say goodbye to the weak, unstable & disconnecting WiFi signal from the 1st floor which I have been getting for the past few years
Goal
- WiFi system that can surround the whole house with WiFi reception
- Smooth handover / Fast Roaming between APs when moving
- I hated the idea of switching between WiFi networks at home, from 1st storey to 2nd story to 2G to 5G to Kitchen to Toilet to You-name-it. Let alone sometimes the signals overlap and you would end up having to power-cycle the WiFi on your smartphone/tablet. It's just endless
- No drilling and long network cables for the obvious reasons of tripping parents including myself
- Which means I have to rely on Wireless backhauls/uplinks
- Adequate local network performance for media streaming Eg: Plex & HTPCs
During that time, I was also tasked with replacing the one and only Linksys WRT-54G Router, into deploying a small-medium scale WiFi system which covers about 80% of the operating areas of an island resort
As I don't have experience in deploying enterprise or small-medium scale WiFi systems, I thought it would be a good chance to learn from changing Home(1)'s system as the infrastructure was similar, just bigger and more APs. (UniFi Controller? What's that?)
Hardware
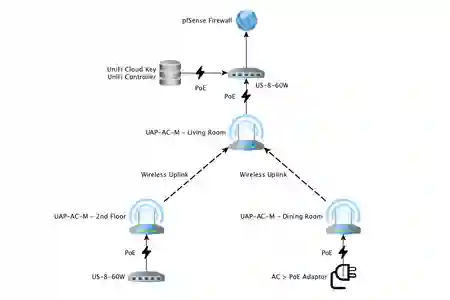
RouterASUSTeK RT-AC68U >> pfSense FirewallControllerUBNT Cloud KeySwitchUBNT Switch 8 - US‑8‑60W x2WiFi APsUBNT UAP-AC-M x3
Network Topology
Experience
- PoE (Power over Ethernet) is a godsend
- Imagine plugging in a LAN cable into the device and it just lights up. Saving me x2 AC adaptors. How cool is that!?
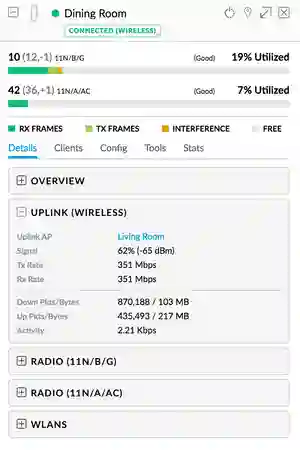
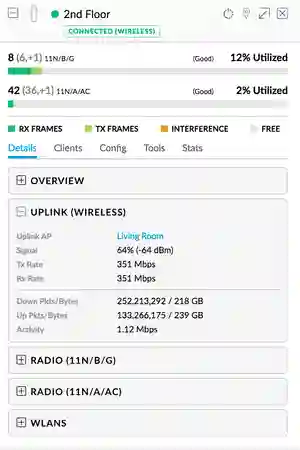
- Roaming between APs was smooth
- You could tell you've roamed to another AP during VoIP calls, but it is very slight. You have to really concentrate to know the difference. Client devices, call quality and noise are variables and I can't provide a more accurate test. If the opposing party was to speak "catty ears", during the roam, you will end up hearing "cat ears" - most of the time "___ ears" - worst case
- Switching between 2.4GHz & 5GHz (Indoors)
- You need to be around 10~15metres to the AP to utilize 5GHz. So far I am happy with this distance. Even if I do drop back to 2.4GHz, my radio is set to HT40 frequency so I do get above 100Mbps WiFi speeds, which is also enough as House(1)'s WAN only has 50Mbps/20Mbps Download/Upload bandwidth
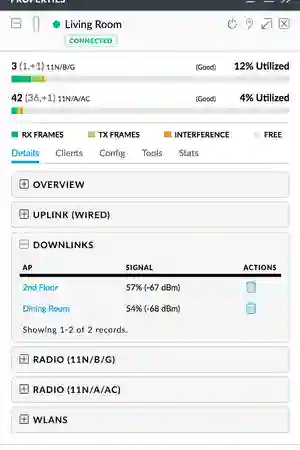
- Backhaul / Wireless Uplink Ping
- 8~10ms between devices
All right, now that I have WiFi reception in the house settled, time to move on to install a shiny new firewall/router
pfSense Router & Firewall
After lots of forum reading, it seems that the UniFi's Security Gateway (USG) is lacking in performance, and the next model becomes a 1U rack. So I went with pfSense
Though my UniFi Controller Dashboard will never show an "All Green" due to the lack of the [Router] Security Gateway, it is comforting to know that it's just aesthetics, and you won't be staring at it forever once everything has been set up and works properly. Who are you going to show it off to anyway other than yourself?
Major reasons for choosing pfSense over the UniFi Gateways other than performance & size was the ability to install packages and upgradability
- Packages
- IDS/IPS - Suricata, Snort
- UniFi Gateways with the latest firmware now includes IDS using Suricata and built nicely into their Dashboard
- As of writing, pfSense and Snort with OpenAppID now has the ability to detect applications in your network (it can block Dropbox or even WhatsApp)
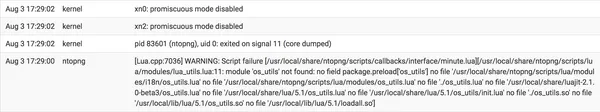
- Monitoring - ntopng
- Has option to export flows to the Elastic Logstash Kibana (ELK) stack
- Captive Portal
- UniFi allows only one captive portal per site. With pfSense, I am able to host an additional captive portal, which makes it a total of 2 captive portals. Island resort scenario: "Guests WiFi" with Vouchers given out by the UniFi controller, while pfSense hosts "Free WiFi" with no authorization
- Upgradability
- Need more RAM? Need a bigger SSD? Definitely sounds easier to upgrade than the USGs
- Or even run pfSense as a VM
- IDS/IPS - Suricata, Snort
Hardware
Unfortunately, I do not have any old unused computer kept in the storeroom. It can be rather limited where I reside (or none at all actually), to find a box that supports AES-NI and has a small footprint. After searching for a while, I decided to go for protectli's FW4A
My pfSense Firewall Router
- protectli FW4A
- Intel Atom® E3845 Quad Core at 1.91GHz
- 4 Intel® Gigabit 82583V Ethernet NIC ports
- AES-NI
- Fanless and Silent
- 8GB RAM
- 250GB SSD
You can check out review video of the Intel® Quad Core Celeron J1900 model
Another which is an Intel 3865U Dual Core at 1.8GHz 6 port model
Do check out Lawrence Systems as his videos are very resourceful and helpful
Experience (pfSense)

Search, Read, Watch, Practical. Repeat X times
One of the gripes that I came across with Community forums is that you will need to read through, filter and try your best to not fall asleep while keeping your fingers crossed that you have searched for the correct term(s). If you are non-tech-savvy, go the USG way, as you can still ask for help from the UBNT Ubiquiti support
- Setting up VLANs
- WAN PPPoE (ISP with VoIP and TV)
- User network
- Guests WiFi with a simple "I accept" no authorization Captive Portal
- Throttle Guests Download bandwidth (via UniFi profiles)
- "Wow, do you need that?" Yes, because my parents host parties that will easily go over 10 guests. Adults with YouTube nowadays
- Site-to-Site OpenVPN with Home(2)
- Remember to restart pfSense after adding the OpenVPN client interface
- Traffic Shaping
- Assign my Synology NAS into low priority. Throttle it down when other devices need the bandwidth
- Snort with OpenAppID
- Block BitTorrent & Tor
- Route device or port to paid 3rd party VPN service (Policy Routing)
- Examples
- Guests WiFi data gets routed to VPN service instead of ISP WAN
- All traffic from IP/device gets routed to VPN service instead of ISP WAN
- Examples
- Squid Transparent Proxy Server (not using anymore)
- Since most traffic nowadays is SSL encrypted. MITM is for extreme cases and you have a way to install certificates on your devices
- Though! It can be really helpful if you are updating multiple Linux servers and have a slow WAN. Since their repositories are mostly HTTP, you do not have to re-download the updates. Ensure Squid is set to cache file sizes bigger than 50MB. Eg: 100MB
- ntopng monitoring
- Ensure VPN is being routed correctly
- Check who is hogging your bandwidth when needed
- Enable SNMP on pfSense and other devices in the network
Enterprise WiFi (for the home)
Research around the web long enough and you are bound to hear or read someone say this: Consumer routers, out of convenience and for whatever reasons, combined Router, Switch, Wireless AP, all into one. Which is true and a very important tip/hint to keep in mind before venturing into the Enterprise field
A layman's quick explanation
- pfSense -
Router+FirewallRouter- Connects to your ISP's WAN (remote Internet) and provides NAT (local private network) to your devicesFirewall- Blocks and allow connections
- UniFi
Controller& DevicesController- Controls, sends bulk configurations to UniFiSwitches&Wireless APsSwitches- Directs network packets/data between DevicesWireless APs- Wireless Access Point, I just think of it as a WirelessSwitch
So what convenience/differences are we talking about that will change our workflow? You will need to separately visit all the different components in your network
Example: If you plan to change a VLAN setting, you will need to change all the VLAN settings on your Switches, Wireless APs in order prior to making any changes in your Router. If you do not have a management VLAN setup and/or do not know what you are doing, you will end up locking yourself out of the configuration UI. This results in pulling your hair out and resetting devices, which is time-consuming and adds up the overall frustration (been there, done that)
Fortunately, the UniFi Controller combines Switches and Wireless APs into one GUI which speeds up the process exponentially depending on how many devices you have. It does not mean much in a home scenario with 10 devices at most
Now imagine setting up x10 Switches because you want to change/add a VLAN ID, and x50 Wireless APs just because you had a WiFi SSID typo. Time duration just snowballed from 30minutes to 24hours or more if you were to set them up individually